Cloudflare Proxy Integration — Blocking Origins and IPs
Fingerprint allows you to filter requests to prevent bad actors from making identification requests using your account. Filtered-out requests do not count toward your Fingerprint billing. However, if you use a Cloudflare integration, those requests can still be proxied through your Cloudflare worker, potentially increasing your Cloudflare costs.
To prevent this, you can block specific IPs or origins at the Cloudflare worker level, using Cloudflare's Web Application Firewall.
Cloudflare Web Application Firewall
- You are limited to 5 WAF custom rules on the Cloudflare free plan.
- In this guide, we use the Cloudflare dashboard to manually create WAF custom rules. You can also create and modify custom rules programmatically using the Cloudflare API.
1. Find URIs to be blocked
Your Fingerprint Cloudfare worker exposes two endpoints — one for downloading the JavaScript agent and one for retrieving identification results. Their paths are random strings compiled from variables provided during the integration setup. You can find these values in the worker's environment variables:
- Go to your Cloudflare account.
- Using the left-hand menu, navigate to Workers → Overview and select your Fingerprint Cloudflare worker.
- On the worker page, switch to the Settings tab and select Variables.
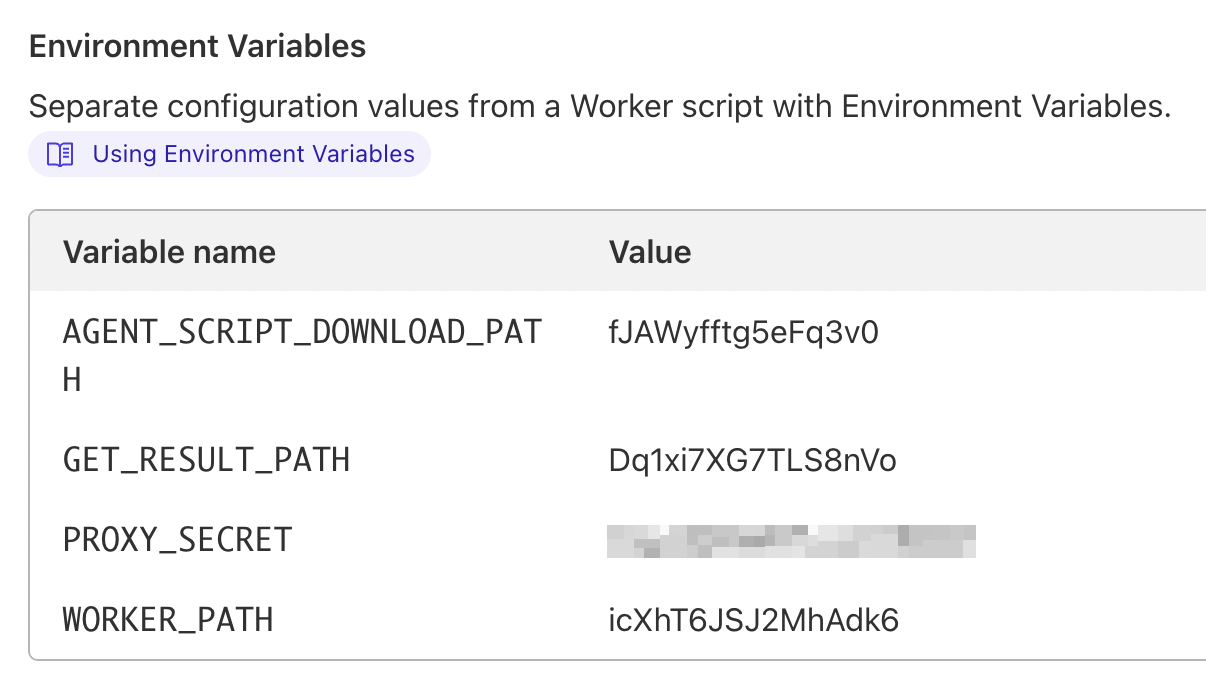
In the worker's environment variables, you will see four variables with random string values.
The worker has two endpoints:
/<WORKER_PATH>/<AGENT_SCRIPT_DOWLOAD_PATH>for downloading the agent/<WORKER_PATH>/<GET_RESULT_PATH>for getting identification results
Replace placeholders in the endpoint patterns above with your worker's environment variables. Using the example in the screenshot, you get the following:
- agent download URI is
/icXhT6JSJ2MhAdk6/fJAWyfftg5eFq3v0 - identification result URI is
/icXhT6JSJ2MhAdk6/Dq1xi7XG7TLS8nVo
2. Create a firewall rule
Create a custom rule in your Cloudflare WAF.
- Inside your Cloudflare dashboard, navigate to Websites → Your website → Security → WAF → Custom rules.
- Click Create rule.
- Enter a name for the rule.
- Use the provided editor to define your rule or click Edit expression to define the rule using the Rules language (examples below).
- Choose
Blockas the rule action. - Click Deploy.
Creating a firewall rule
Block requests from specific IP addresses
For example, to block IPs 111.111.112.113, 114.112.222.33, and the entire 211.12.82.0/24 subnet for worker routes /icXhT6JSJ2MhAdk6/fJAWyfftg5eFq3v0 and /icXhT6JSJ2MhAdk6/Dq1xi7XG7TLS8nVo, use the following expression:
(
ip.src in {111.111.112.113, 114.112.222.33, 211.12.82.0/24}
and
(
http.request.uri.path eq "/icXhT6JSJ2MhAdk6/fJAWyfftg5eFq3v0"
or
http.request.uri.path eq "/icXhT6JSJ2MhAdk6/Dq1xi7XG7TLS8nVo"
)
)Block requests from specific origin and referer
origin and refererFor example, to block requests from example1.com for the same worker routes, use the following expression:
(
(
http.request.uri.path eq "/icXhT6JSJ2MhAdk6/fJAWyfftg5eFq3v0"
or
http.request.uri.path eq "/icXhT6JSJ2MhAdk6/Dq1xi7XG7TLS8nVo"
)
and
(
any(http.request.headers["origin"][*] == "https://example1.com")
or
any(http.request.headers["referer"][*] contains "https://example1.com/")
)
)You need to block requests by referer in addition to origin because some types of requests do not include the origin header.
See Cloudflare documentation for more details.
Cloudflare limitations
- Each rule expression can contain up to 4096 symbols.
- The number of custom rules depends on your customer plan.
Updated 26 days ago
