Search bot request filtering
Allow basic search bots filtering through a single switch in the Request Filtering Dashboard section
Search bots generate legitimate internet traffic allowing search engines to index your website. But you might not want search bots to trigger Fingerprint Identification or Smart Signals processing.
Although you can filter requests based on the User-Agent header, you would need to manage your list of all different search bot User-Agent strings. Instead, we keep and update our own list of search bot filtering rules that can be turned on or off through a switch in the Dashboard.
Search bots that are filtered through this setting then behave in the same way as other request filtering rules and you don't get billed for them. Keep in mind that we won't return any information except requestId in those cases.
Search bots filtering based on
User-Agentis a basic mechanism we provide for free to filter out commonly encountered and generally well behaved search bots.Because of its simplicity, it might introduce both false positive and false negative cases. If you need better protection against sophisticated bots, check out our Smart Signals that contain a paid Bot Detection product.
Configuration
Search Bots Filtering can be turned on or off in our Dashboard.
- Navigate to Dashboard > Security and switch to the Bots tab.
- Enable Exclude Search Bots to start filtering search bots from your billable API calls.
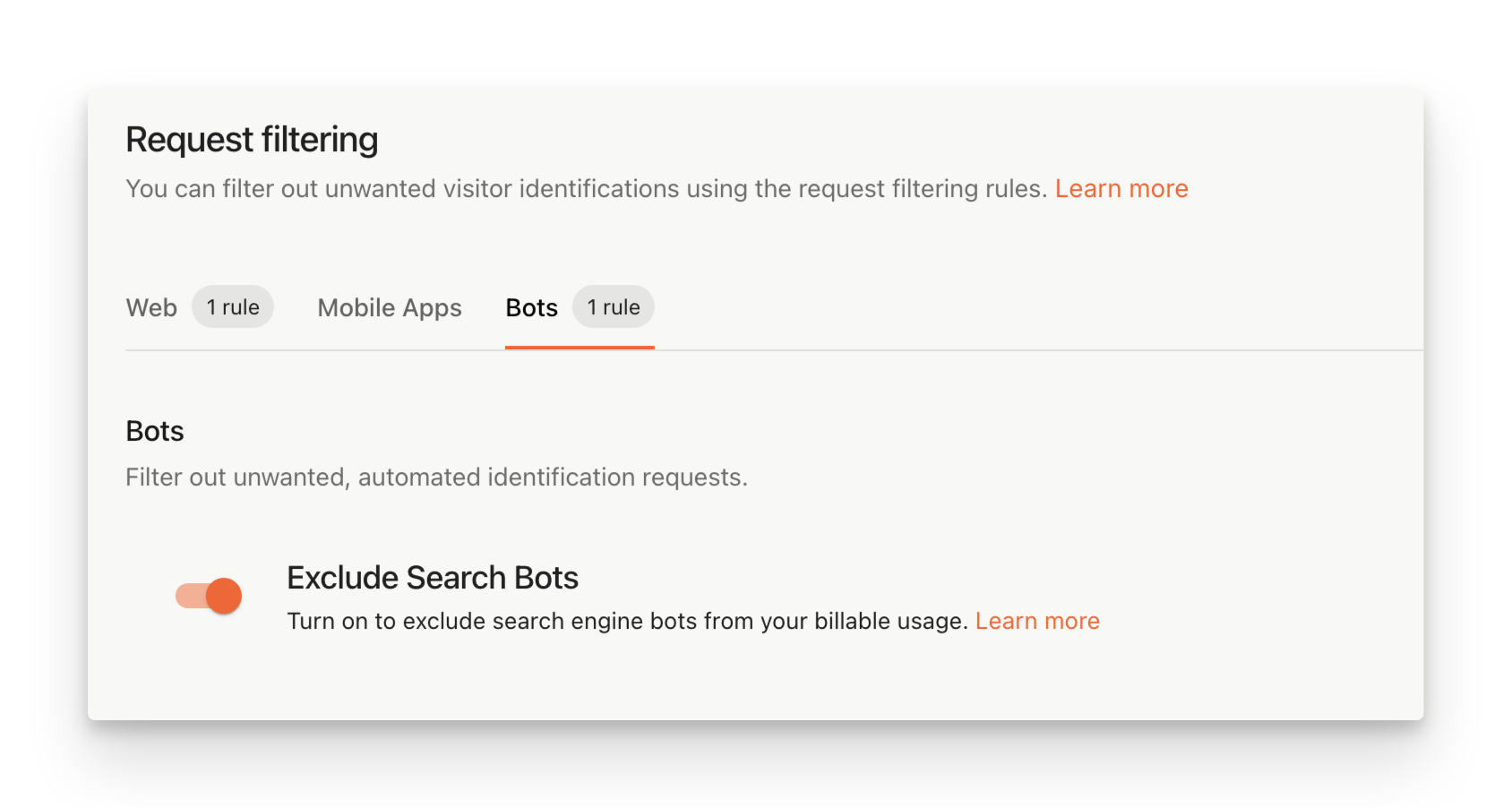
Dashboard - Search Bots Filtering
List of supported search bots User-Agent strings
User-Agent stringsThe list of search botsUser-Agent strings we support is public and we keep it updated based on the currently supported User-Agent strings. The following table contains all supported User-Agent strings with their respective information sources.
Owner | User-Agent (Substrings) | Public doc |
|---|---|---|
Mail.ru |
| |
Microsoft |
| |
Apple |
| |
Huawei |
| |
Naver |
| |
Yahoo |
| |
Baidu |
| |
Sogou |
| |
Exalead |
| |
Coccoc |
| |
Seznam |
| |
| ||
Yandex |
| |
Bytedance |
| |
Duckduckgo |
| |
Ahrefs |
| |
| ||
| ||
Cincraw |
| |
Semrush |
| |
Seekport |
| |
Amazon |
| |
DataDog |
|
Updated about 1 month ago
